Quantum Cryptography: The Future of Secure Communication
Over the past decade, there has been a growing interest and developments in quantum cryptography. This is a new field of cryptography that uses the principles of quantum mechanics to create secure communication channels. Quantum cryptography is still in its early stages, but it has the potential to revolutionize the way we communicate.
Traditional cryptography is based on the idea of using mathematical algorithms to encrypt and decrypt messages. These algorithms are designed to be very difficult to break, but they are not impossible. With enough time and computing power, an attacker could eventually break any traditional cryptography algorithm.
Quantum cryptography, on the other hand, is based on the principles of quantum mechanics. Quantum mechanics is a branch of physics that deals with the behavior of matter and energy at the atomic and subatomic level. One of the key principles of quantum mechanics is the uncertainty principle, which states that it is impossible to know both the position and momentum of a particle with perfect accuracy.
This uncertainty principle can be used to create a very secure communication channel. When two parties want to communicate securely, they can use quantum cryptography to share a secret key. This key is used to encrypt and decrypt messages. If an attacker tries to intercept the messages, they will not be able to read them because they will not have the secret key.
The reason why quantum cryptography is so secure is because it is based on the laws of physics. The uncertainty principle is a fundamental law of physics, and it cannot be broken. This means that quantum cryptography is immune to attack by even the most powerful computers.
Quantum cryptography is ideal for applications where security is critical, such as government communications, financial transactions, and military communications. In these applications, it is essential to be able to communicate securely, and quantum cryptography provides the highest level of security available.
Here are some specific examples of how quantum cryptography could be used:
- Government communications: Quantum cryptography could be used to protect government communications from being intercepted by foreign governments or terrorist organizations.
- Financial transactions: Quantum cryptography could be used to protect financial transactions from being hacked. This would help to prevent fraud and protect customer data.
- Military communications: Quantum cryptography could be used to protect military communications from being intercepted by enemy forces. This would help to ensure the safety of military personnel and protect sensitive military information.
Quantum Cryptography Protocols

Quantum Key Distribution (QKD)
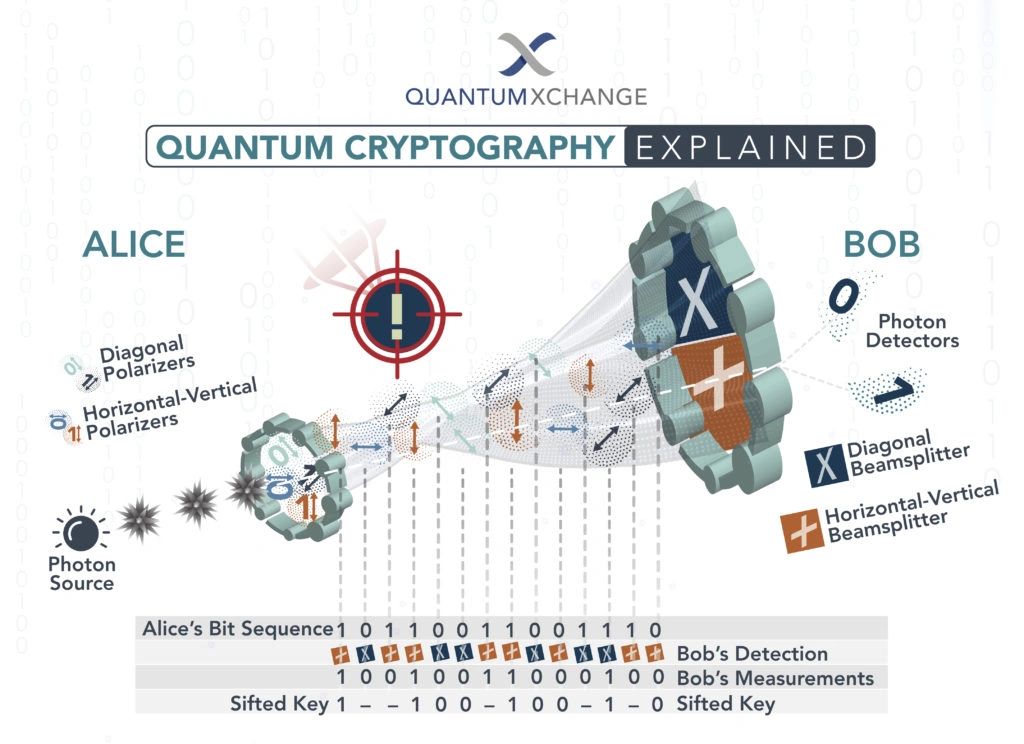
QKD is a protocol that allows two parties to share a secret key over an insecure channel. This key can then be used to encrypt and decrypt messages.
The way QKD works is by using qubits to encode the secret key. Qubits are quantum mechanical objects that can exist in a superposition of states. This means that they can be both 0 and 1 at the same time.
The qubits are sent through a quantum channel, which is a communication channel that is designed to protect the information from being intercepted. If an attacker tries to intercept the qubits, they will disrupt the superposition of the qubits. This will cause the information to be lost, and the attacker will not be able to read it.
The two parties, Alice and Bob, can then use the qubits to create a shared secret key. Alice and Bob will each measure the qubits they receive, and they will compare their results. If their results are the same, then they know that they have shared a secret key.
Quantum Secure Direct Communication (QSDC)
QSDC is a type of quantum cryptography that allows two parties to communicate securely over an insecure channel. This means that the messages cannot be read by anyone else, even if they are intercepted.
The way QSDC works is by using qubits to encode the messages. Qubits are quantum mechanical objects that can exist in a superposition of states. This means that they can be both 0 and 1 at the same time.
When qubits are used to encode messages, they are sent through a quantum channel. This is a communication channel that is designed to protect the information from being intercepted.
If an attacker tries to intercept the information, they will disrupt the superposition of the qubits. This will cause the information to be lost, and the attacker will not be able to read it.
There are two main types of QSDC protocols:
- Bennett-Brassard 1984 (BB84) protocol: This is the first QSDC protocol that was developed. It is based on the principle of quantum key distribution (QKD).
- Ekert 1991 protocol: This is another QSDC protocol that is based on the principle of quantum entanglement.
Both BB84 and Ekert protocols are very secure, but they are also very complex. This has made it difficult to implement them in practice.
However, there has been a lot of progress in recent years in the development of QSDC protocols. Today, there are a number of QSDC protocols that are more practical and easier to implement.
QSDC has a number of potential applications, including:
- Government communications: QSDC could be used to secure government communications, such as classified military communications.
- Financial transactions: QSDC could be used to secure financial transactions, such as online banking and credit card transactions.
- Medical records: QSDC could be used to secure medical records, such as patient records and test results.
QSDC is a promising new technology that has the potential to revolutionize the way we communicate. It is still in its early stages, but it is developing rapidly. As QSDC protocols become more practical and easier to implement, they will become more widely used.
Here are some additional details about QSDC:
- Security: QSDC is very secure. It is based on the laws of physics, which makes it very difficult to hack.
- Complexity: QSDC is more complex than traditional cryptography. This has made it difficult to implement QSDC in practice.
- Applications: QSDC has a number of potential applications, including government communications, financial transactions, and medical records.
- Future: QSDC is a promising new technology that has the potential to revolutionize the way we communicate. As QSDC protocols become more practical and easier to implement, they will become more widely used.

History of Quantum Cryptography
The history of quantum cryptography can be traced back to the early 1970s, when Stephen Wiesner first proposed the idea of using quantum mechanics to create secure communication channels. However, it was not until the 1980s that the first practical quantum cryptography protocols were developed.
One of the most important early developments in quantum cryptography was the BB84 protocol, which was developed by Charles Bennett and Gilles Brassard in 1984. The BB84 protocol is a quantum key distribution (QKD) protocol that allows two parties to share a secret key over an insecure channel.
Another important early development in quantum cryptography was the Ekert protocol, which was developed by Artur Ekert in 1991. The Ekert protocol is another QKD protocol that is based on the principles of quantum entanglement.
In the years since the development of the BB84 and Ekert protocols, there has been a great deal of research in quantum cryptography. Today, there are a number of different quantum cryptography protocols that are in use or under development.
The Outlook of Quantum Cryptography
The outlook for quantum cryptography is very bright. As quantum computers become more powerful, quantum cryptography will become even more important. This is because quantum computers will be able to break traditional cryptography algorithms, but they will not be able to break quantum cryptography.
In addition, quantum cryptography is being used in a number of new and innovative ways. For example, it is being used to develop secure voting systems, to protect medical records, and to create more secure financial transactions.
Overall, the outlook for quantum cryptography is very positive. It is a promising new technology that has the potential to revolutionize the way we communicate and interact with the world around us.




